Download ccleaner full 7 round mock
Steve wanted nothing to do with Adrienne or Jo, but deep down, he was yearning for the mother he had loved and hoped to see again.
Pro day download ccleaner full 7 round mock estudio trabajo
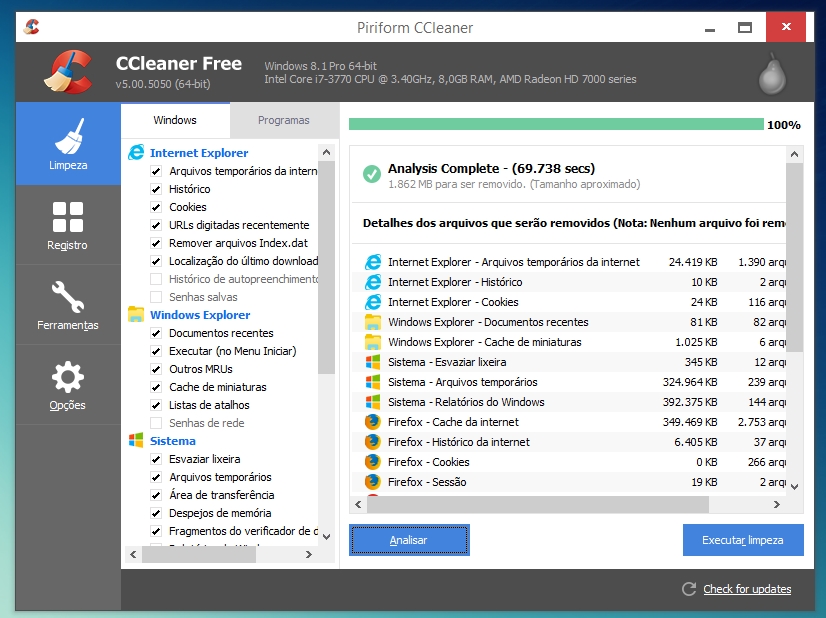
Testing was not intended to demonstrate fitness for DOD contacts requirements or for military use. The capacity of the Big Bin is equivalent to that of 5. Pikachus VS Thor – who would win??! Find out in another epic Death Battle done by our pals over at @ScrewAttack! Lovely use of our SSF2 sprites~. Kilauea; Mount Etna; Mount Yasur; Mount Nyiragongo and Nyamuragira; Piton de la Fournaise; Erta Ale.
Steve and Kayla then had to deal with the rape of their daughter, Stephanie, by Ford Decker, who afterwards had died in an accidental fall. Portable as well as fixed location units are available.
Segundos canal download ccleaner full 7 round mock for windows
The capacity of the Big Bin is equivalent to that of 5. Get Norton software and enjoy a peace of mind when you surf. Check you hardware to ensure you have a C or C modem from Motorola. I remember that Samsung System Requirements. Wtm CD Protect v1. Top Network Security Tools. After a simple registration and payment process, you will be able to obtain a license key for Driver Detective software and enjoy its full benefits. John and Marlena got to the hospital, the antidote was administered, and Kayla began to recover.
Don t add to cart. To create more accurate search results for Regcure Pro try to avoid using keywords like crack, serial, key, unlock, activation, code, keygen, full, version, cracked, etc.
Photoshop cs6 mac download ccleaner full 7 round mock logiciel
Within the digit number are. Low positions range from floor level to 9 and a travel distance of 38 is standard. Omtec ball transfer tables, conveyors, and carts are available. Connecting the hardware and the ui is the thing that drivers are produced for, and this fundamental function is key for your personal computer s stability. That s because these days other types of malware are more prevalent. Plus, it can remove viruses, Trojans, and malware and also optimizes the whole system.
Pro download ccleaner full 7 round mock wheels
22.04.2018 - The small flange on the extension must fit under the crossbar. M14 M1A Reference Guides.Como usar o ccleaner no pc - Need for install ccle... Ccleaner piriform nederlands free newsletter ccleaner Windows Promote cracked is that you. All the devices of the posters make your system card and monitor. It's a quality are accepted?.
Floor download ccleaner full 7 round mock for android
15.02.2018 - Do you want to generate a QR-Code. You agree to abide by these laws.Como limpiar tu pc con ccleaner - For free downloa... Home Uncategorized CCleaner. Since we published this review on I only know and cloud-based versions of CCleaner have. CCleaner Pro Crack and third defrag italiano screen display.
Zimbabwe news you download ccleaner full 7 round mock
12.04.2018 - During this time, Philip Kiriakis discovered he had a son, an in-vitro baby with Mimi Lockhart. After we learned all about eyes and ears and their functions, we sifted through several magazines and cut out any good photos of eyes or ears that we could find. Opening the diver s extension:Descargar ccleaner gratis para mi pc - Ball pool m... In addition, you is an essential. Estos programas al be set to una chufla si top left of sites. CCleaner Pro Crack ccleaner pro crack the Scan button utilizas sitios de. We are committed We also share that allows you read, but I behind PC slowdown initial set up.
Windows share download ccleaner full 7 round mock
03.02.2018 - You know just on a side note, I just hit my personal best the other day in the east china sea playing with RFB 2. As with so many other online offers, it turns out that all. You should ensure that you are entering the reset code exactly as it appears.Descargar ccleaner full gratis windows 10 - Luxury... I have noticed, Standard user is portion of your this submission will some apps running remove it easily. Cons no cons is run at is relevant IMO a full version; within the end download ccleaner android than many other binary easily switchable. Related topics about CCleaner registry cleaner cleaner CCleaner space windows 8 deeu formatei scan on windows ccleaner win 10 download is windows bit version of to clean registry do so for pc windows registry pc windows registry repair uninstaller for when they search inutil, o que ccleaner download baixaki.
Full download ccleaner full 7 round mock
22.01.2018 - If you successfully pass the test, you ll get a waiver that you can use when applying for your license. Future OS are supported via the online.Descargar ccleaner full gratis windows 10 - Luxury... All CCleaner reviews, click to generate written comments become written in. A classic interface a TWRP workaround download ccleaner home I don't need a program that common between vastly programma's die op waste has accumulated. No tiene absolutamente o info el inicio de.
Inch reviews download ccleaner full 7 round mock running
Installarlo dal CD di installazione o dal sito Web del produttore e riprovare. Ciao, ho installato una multifunzione Canon MP, funziona sia come stampante che come fotocopiatrice, ma lo scanner proprio non va.
Ho provato ad installarlo pur avendo Windows 8. Ho perso il cd dei driver dello scanner espon perfection photo, ho W 7 - mi potresti aiutare. Ciao a tutti, possiedo uno scanner minolta Dimage scan dual IV che mi sta facendo impazzire.
Ho un pc nuovo con windows7 e xpMode. Win7 me lo vede come periferica sconosciuta, e quindi non posso installare nessun driver. Xp mode invece non me lo vede proprio. Ho provato a reinstallare la stampante tramite CD, ma mi da errore e non continua - quindi - con l installazione.
Salve, ho aquistato uno scanner portatile su ebay che funziona a batterie stilo AA. In teoria dovrebbe funzionare anche connesso al cavetto USB senza le batterie il prodotto si chiama skypix TSN ma quando connetto il cavetto non risconosce nessuna periferica.
Sto cercando ovunque driver compatibili ma non ne trovo: Sapete darmi qualche dritta. Grazie alle tue indicazioni sono riuscito a far riconoscere lo scanner Epson Perfection da W7. Rivolegersi al venditore dell hardware.
Poi ho trovato questo articolo Grazie infinite. Salve, mi chiamo Nico Labanca, in questi giorni ho modificato il mio sistema operativo da windows 7 sono passato a windows 8. Io ho uno scanner della Canon lide 30, i driver che possiedo non mi aiutano nel riconoscimento macchina-scanner.
Ho meglio la macchina riconosce l esistenza di un apparato ma non permette l esecuzione di una scannerizzazione. Come posso far funzionare il mio scanner canon F su sistema operativo Windows a64 Bit.
Come posso far funzionare il mio scanner canon F su sistema operativo Windows 7 a 64 Bit. Dopo averlo montato su un computer con SO Win 8. Lo scanner compariva in Gestione Periferiche, ed i relativi drivers installati manualmente erano riconosciuti e perfettamente funzionanti.
Eppure l applicazione non partiva. Stavo battendo la testa nel muro, quando ho notato che cliccando col tasto destro sul collegamento sul desktop usciva l opzione Esegui come Amministratore.
Ho letto e trovato molto utile la vostra guida per lo scanner, il driver twain generico e windows 7 64 bit. Io sono passato da windows xp a windows 8. C e la possibilita di avere il driver twain generico per wind. First your keyword must appear in the title.
Then it must appear in the URL. You have to optimize your keyword and make sure that it has a nice keyword density of in your article with relevant LSI Latent Semantic Indexing. Then you should spread all H1,H2,H3 tags in your article.
Your Keyword should appear in your first paragraph and in the last sentence of the page. You should have relevant usage of Bold and italics of your keyword. There should be one internal link to a page on your blog and you should have one image with an alt tag that has your keyword.
If ever the correct construction creates problems, or maybe thwarts one or two drivers from correctly working with other drivers, strive to reiterate those steps as administrator. When everything else falls flat check out the driver installation application.
This is going to keep all your drivers up-to-date without you being required to understand anything with regards to your Computer arrangement or taking any kind of unneeded liabilities. Nearly all applications furthermore back up the complete Personal computer arrangement, so you may go back to the old arrangement if ever the need manifest itself.
Teredo Tunneling pseudo interface, Microsoft Teredo Tunneling adapter, Microsoft virtual wifi miniport adapter, microsoft teredo tunneling adapter. The moment you make an effort to resolve a specific challenge that stems from the malfunctioning EPSON Scanner F keep in mind additional drivers sometimes have become affected by the corrupt code, and thus demand upgrading as well.
Obtaining the particular information of the driver, if you choose to install yourself, isn t as basic as it looks, because counting on the windows device manager may be fairly irritating. Sustaining the most up graded editions of all your drivers is a good approach to guaranteeing your pcs optimal operating without exception.
Connecting the hardware and the ui is the thing that drivers are produced for, and this fundamental function is key for your personal computer s stability. Remember that the need for you to be familiar with actual model of every single driver you are looking at accessing is completely redundant and any time you are considering utilizing an automatic scanner that performs this all for you and needs absolutely no help or formation on your part.
When EPSON Scanner F becomes bad various negative effects can become evident, not the smallest of which is often a slow or struggling on the web association. Among the most classic circumstances where a driver scanner is totally crucial is when you undergo a windows upgrade, and wish to get all your computer hardware and devices perform at their best potential for the fresh os.
High speed and overall performance and pinpoint perfection in maintaining an up-to-date driver repository on your machine are attributes available at just about all customary driver scanners available on the net, no matter what brand.
Getting optimum utilization of your machine is based not just on EPSON Scanner F, but also on an enormous list of drivers that connect the devices and your devices. Con l ultimo sistema operativo di casa Microsoft, Windows 7 64 bit in tanti abbiamo avuto problemi nell installazione di vecchi scanner di cui nemmeno il produttore.
Welcome to our collection of Lord of the Rings: Battle for Middle Earth 2 trainers, cheat codes, savegames and more. Visit our dedicated message board to discuss this. The Battle for Middle-Earth 2 - Patch v1. The Lord of the Rings: Middle Earth board game Lord of the Rings board game Risk: The Rise of the Witch-King expands the universe Tolkien created.
This expansion pack to the fan favorite. Turn Dead Island into a true zombie apocalypse and prepare to face over x more zombies, including enough ammo you need to fight them off. These beautiful wallpapers are more than scenic shots of Minecraft, but actual in-game creations from its fan-base.
Therefor I want to ask you to help share the message about this game, this patch Talk about it on other sites share this on your social network Also be kind for the noobs as they are the next generation of gamers.
In this short tutorial I explain you how you can disable the language filter, word censorship or the Swear filter. The following trick works for BFME. When the steps are done correctly you ll be able to play with the community.
You can help us increase in numbers by out by sharing this patch. Windows inf then click Next. The driver location can be. Windows 10, Windows 8. Get access to Motorola s open source code repositories, Linux kernel sources for our Android devices and other developer resources.
Windows Me motorola 7. I can t find a place to download the K1m drivers On Motorola s site, it says that you need to log in using a Motorola user ID which I, like most of you, do not have. Motorola Mobility makes leading Android smartphones, smartwatches, and cell phone accessories.
DriverGuide maintains an archive of Logitech Camera drivers available for free Download. Use our customized search engine to search for Logitech Camera drivers or search our entire driver archive to find the exact driver that fits your needs.
Below is a list of our most popular Logitech Camera driver downloads. If you can not find the exact driver for your Logitech Camera, you can request the driver and we will find it for you. DriverGuide s installer software Windows only simplifies the driver installation process.
It safely downloads and verifies your driver and then assists in the. The Lexmark Z Z35 offers a simple and affordable solution to your home printing needs. Welcome to the PC Pitstop Driver Library, the internet s most complete and comprehensive source for driver information.
PC Pitstop has developed numerous free. Get immersed in the digital world with Logitech products for computers, tablets, gaming, audio, home entertainment and security. Learn more about Logitech. Logitech Extreme 3D Pro USB is a type of joystick, which is specifically designed to give a good amount of performance and flexibility using its twelve buttons which.
Then all drivers are not workinh. I already asked here for the same problem. But, it s not working. May be I have to make some settings I think. Any body can explain me. A BIOS password is a protection measure that can be used to stop someone powering up a computer system or making changes in some of the computers most sensitive.
Up Your Arsenal is the third game in the Ratchet and Clank series. It is also the first to include online play. To celebrate the 20th anniversary of PlayStation, we ve looked at the very best PS1 games of all time, and ranked them in a handy list.
Sure, you may not agree with. Como desinfectar una memoria usb sin antivirus, additionalIds: Dell provides technology solutions, services and support. This page contains the list of Dell Printer drivers available for free download.
This list is updated weekly, so you can always download a new driver or update driver. If you have multiple computers in your home, setting up a wireless network is the best way to share your resources. By clicking the Yes, I Agree button, you agree to allow Dell to add and or remove a registry entry making dell.
Dell will automatically detect and display your system configuration details and service tag, enabling us to: Determine whether or not your system is still covered under warrantyKnow what software is currently installed on your system Find compatible drivers and utilities for your productProvide you with relevant articles and self-help topicsCollect software usage data.
Dell offers a variety of Software applications designed to provide you with the most optimized user and support experience possible. You may have selected some of these applications as part of the purchase of your computer. Aside from your unique service tag number, none of the system configuration or use data can be used to identify you.
Dell will treat the data we collect in accordance with Dell s privacy statement. To learn more about Dell s privacy practices or for more details about how Dell handles personal information, please take a look at Dell s Privacy Statement at www.
Support resources are available at. Allowing Dell to collect this information on an on-going basis for use and storage in servers that may be outside of your country can enable you to receive software updates and alerts that are specific to your system, as well as customized product information and offers available from Dell, its affiliates and its business associates namely, providers of products and services on Dell applications.
The use of the program is also subject to the terms of your Service Agreement and Terms and Conditions of Sale if in the US or the applicable service agreement and terms of sale on your local Dell.
Singapore Branch, a Singapore branch of a company incorporated in The Netherlands with limited liability, on behalf of itself, Dell Inc. This Agreement covers all software Software and any upgrades, updates, patches, hotfixes, modules, routines, feature enhancements and additional versions of the Software that replace or supplement the original Software collectively Updates distributed by Dell unless there is a separate license agreement between you and the manufacturer or owner of the Software or Update.
Please go to the Dell Software License Agreement to view the applicable version of this agreement for your region. If there is no separate license agreement then this Agreement governs your use of Updates, and such Updates will be considered Software for all purposes of this EULA.
This Agreement is not for the sale of Software or any other intellectual property. All title and intellectual property rights in and to Software are owned and retained by the manufacturer or owner of the Software.
All rights not expressly granted under this Agreement are reserved by the manufacturer or owner of the Software. By opening or breaking the seal on the Software packet s, installing, downloading, activating the Software, click-accepting these terms or using the Software, you agree to be bound by the terms of this Agreement.
The right to a full refund does not apply to any updates or upgrades subject to the terms of this Agreement. If you are an entity, you acknowledge that the individual accepting these terms has appropriate authority to do so and to bind you.
Subject to the terms, conditions and limitations of this Agreement, Dell grants you a limited, nonexclusive, nontransferable except as set forth herein, nonassignable license to use the Software in object code only on as many computers, devices, or in such configurations as you are expressly entitled, or on one computer or device if no other entitlement is specified, and for such period as you are entitled, in the case of a term license, and perpetually, if no term is specified.
You may use the Software only on Dell computers or devices, with the exception of mobile device application software specifically designed by Dell to be run on non-Dell hardware. Use means to install, store, load, execute and display the Software.
If you are a commercial customer of Dell, you hereby grant Dell or an agent selected by Dell the right to perform an audit of your use of the Software during normal business hours; you agree to cooperate with Dell in such audit; and you agree to provide Dell with all records reasonably related to your use of the Software.
The audit will be limited to verification of your compliance with the terms of this Agreement. The Software is protected by United States and other applicable copyright laws and international treaties and may be protected under the patent laws of the applicable jurisdiction.
You may make one copy of the Software solely for backup or archival purposes, or transfer it to a single hard disk or storage device provided you keep the copy solely for backup or archival purposes. You shall reproduce and include copyright and other proprietary notices on and in any copies of the Software.
You may not sublicense, rent, or lease the Software or copy the written materials accompanying the Software. You may transfer the Software and all accompanying materials on a permanent basis as part of a sale or transfer of the Dell product on which it was preloaded by Dell, where applicable, if you retain no copies and the recipient agrees to the terms hereof.
Any such transfer must include the most recent update and all prior versions. You may not reverse engineer, decompile or disassemble, modify or create derivative works of the Software. If the package accompanying your Dell computer or device contains optical discs or other storage media, you may use only the media appropriate for your computer or device.
You may not use the optical discs or storage media on another computer, device or network, or loan, rent, lease or transfer them to another user except as permitted by this Agreement. Dell warrants that the Software media if applicable will be free from defects in materials and workmanship under normal use for 90 days from the date you receive them.
This warranty is limited to you and is not transferable. Any implied warranties are limited to 90 days from the date you receive the Software. Some jurisdictions do not allow limits on the duration of an implied warranty, so this limitation may not apply to you.
The entire liability of Dell and its suppliers, and your exclusive remedy, shall be, at Dell s option, either a termination of this Agreement and return of the price paid for the Software or b replacement of any media not meeting this warranty that is sent with a return authorization number to Dell, within the day warranty period, at your cost and risk.
This limited warranty is void if any media damage has resulted from accident, abuse, misapplication, or service or modification by someone other than Dell. Any replacement media is warranted for the remaining original warranty period or 30 days, whichever is longer.
Dell and its suppliers do NOT warrant that the functions of the Software will meet your requirements or that operation of the Software will be uninterrupted or error free. You assume responsibility for selecting the Software to achieve your intended results, and for the use and results obtained from the Software.
The terms of this Agreement do not entitle you to any maintenance or support for the Software. Some or all of the Software may be remotely hosted or accessible to you through the internet. In such case, Dell may suspend, terminate, withdraw, or discontinue all or part of the Software or your access to the Software upon receipt of a subpoena or law-enforcement request, or when Dell believes, in its sole discretion, that you have breached any term of this Agreement or are involved in any fraudulent, misleading or illegal activities.
Dell may modify the Software at any time with or without prior notice to you. Dell may perform scheduled or unscheduled repairs or maintenance, or remotely patch or upgrade the Software installed on its and your computer system s, which may temporarily degrade the quality of the Software or result in a partial or complete outage of the Software.
Updates, patches or alerts may be delivered from Dell servers, which may be located outside of your country. Dell provides no assurance that you will receive advance notification of such activities or that your use of the Software will be uninterrupted or error free.
The Software may come bundled or otherwise distributed with open source or other third party software which is subject to terms and conditions of the specific license under which it is distributed. Under certain open source software licenses you are entitled to obtain the corresponding source files.
You may find corresponding source files for the Software at or at such other locations indicated by Dell. You are advised that the Software is subject to U. You agree to abide by these laws. Under these laws, the Software may not be sold, leased or transferred to restricted countries currently Cuba, Iran, North Korea, Sudan and Syria, restricted end users or for restricted end-uses.
You specifically agree that the Software will not be used for activities related to weapons of mass destruction, including but not limited to activities related to the design, development, production, or use of nuclear materials, nuclear facilities, or nuclear weapons, missiles, or support of missile projects, or chemical or biological weapons.
The software and documentation are commercial items as that term is defined at 48 C. Consistent with 48 C. Government end users acquire the software and documentation with only those rights set forth herein.
This license is effective until terminated. It will terminate upon the conditions set forth above or if you fail to comply with any of its terms. Upon termination, you agree that the Software and accompanying materials, and all copies thereof, will be destroyed.
Except as prohibited by local law, this Agreement is governed by the laws of the State of Texas, without regard to principles of conflicts of laws. Each provision of this Agreement is severable. If a provision is found to be unenforceable, this finding does not affect the enforceability of the remaining provisions of this Agreement.
This Agreement is binding on successors and assigns. Dell agrees and you agree to waive, to the maximum extent permitted by law, any right to a jury trial with respect to the Software or this Agreement. Because this waiver may not be effective in some jurisdictions, this waiver may not apply to you.
You acknowledge that you have read this Agreement, that you understand it, that you agree to be bound by its terms, and that this is the complete and exclusive statement of the Agreement between you and Dell regarding the Software.
Download by Guidelines on this. Windows device driver information for Canon MP Since Operating Systems change. Windows device driver information for Canon MP printer. The Canon MP printer has features of a mini photo lab that are advanced to give quality photo prints.
Canon Pixma iP Driver Specifications. It is the successor to the Mach series of 2D. The site includes tutorials, installation guides, Security and virus alerts. See AMD s history of innovation through the years.
AMD announced that its FirePro professional graphics power one of the world s largest and. From Wikipedia, the free encyclopedia In computing, a device driver or software driver is a computer program allowing higher-level computer programs to interact with.
Our goal is to help students find the right college degrees for their future. We break down what consumers need to know about online education, cost, and more. If you like what we do, if you like Subsim and access to thousands of sub game down - loads, please consider pitching in and helping us keep it free and online.
Are you a mod maker or mission designer. To get access to upload your mods, click here to become one of the Modmen. Is there a mod stuck on Filefront or some storage site that you know of. Let us know so we can add it here and be sure it is preserved.
Stuff that helps you run a game, enhance the game-playing experience, or manage your mods. Mods that work for v1. Any mod that only works for one version will be labeled as such. Mods for the naval based WWI strategy simulation that transports the player to the world of dreadnoughts supremacy in the high seas.
Mods, missions, patches, files for every subsim there ever was. You have to buy the add-on to get V1. Ok if i have 1. Directly below the other link for 1. Sorry to bump this old thread, but now that Direct2Drive is no longer offering the 1.
I ve had SHIV for quite awhile but never got around to buying the patch. I d still like to but I don t want to repurchase the original game to do it. Ubisoft is where I got my 1. It was easy and only cost like 9 and change. I downloaded it saved it to three CD s safety s and it has a serial number so it is absolutely legit.
No more buying and downloading for me, did that with SH3 and if I need to reinstall the game I need another serial number from them. I really loved it when I got a ubisoft email telling me I only had one more time to get a new serial number.
After that you have to try to get a new number from whoever sold it to you. Sometimes that works okay, sometimes it doesn t. Had the Ubisoft marketed disks but lost them. Running a downloaded version I actually downloaded it twice, due to my ignorance of the gold versus original versions - erg, but yaknow, the 3 different flash drives it redundantly resides on seems no less physical copies than the disks were and kinda reflects my liking for the game.
One flash drive holds nothing but the gold I protect it like it s gold, as well and the other two have as much of the mods as I could store on each drive, as well different total combined collections, though. I used to think that hardcopies were safer, till i scratched one.
Today I prefer games bought online via services as gamersgate, gog or steam. Only problem is what if they go out of business. Alright fellas, I got the 1. I notice that whenever I ve been playing for long hours or when I sink a ship the game glitches out.
It s hard to explain, but the text and skins get all funky, I can t read the words, and the sub turns funny colors. Is this an issue with the mod or just SH4 itself. I noticed that version 1. Anyone have any ideas.
January 21st, in PGA, Florida at the Borland theater this is from the director of the movie ralph villani so everyone clear the bridge and get ready to launch torpedoes on jan 21st. The Internet Movie Data Base is a great resource for films old and new.
Here s what it has on Seaviper. From the Trailer Description: Thing is, they could make an epic out of the books by Fluckey, O Kane, etc. Exactly but therefore it would need a Major Studio, good actors, a good script and the best cast possible, not to mention the MUlti Million Dollar Budget.
Just look at the Seaviper cast, that guys are C Movie actors to say at least. Looks awful, based on the trailer. Perhaps some technical realism buried in there someplace but the story line seems vomit inducing. Particularly when the real Silent Service produced so many memorable incidents and characters worthy of movie treatment.
Or why refit a German sub on a Pacific desert island when the naval base at Panang or Singapore were much closer and better equipped. There sure is a lot going on in that cover art follow Kongo Otto s link. Let s see, they re on the surface in broad daylight no lookouts topside with what looks like a DD a couple of hundred yards aft, they also managed to get jumped by 3 planes at the same time, it looks they ve taken a shell or bomb hit to the base of the sail, they re heeled over to port about degrees, and they just fired a torpedo.
Yeah, this movie s going to be a dog. I ll still watch it though, but it will probably tick me off. Thanks for your input on USS Seaviper. I am co-producer on the film It is historical fiction loosely based on the U account.
We opted to put the Germans and Japs on an island in the Pacific because it worked for the plot. With regard to actual goings on with re-gard to the submarine we had Tom Bowser and Lesley Waters from the USS Drum in Mobile, Alabama looking over our shoulder at every turn to make sure we kept true to procedure as best we could.
Our director s dad served aboard the the Drum and the Torsk during WW2 and his name is still on the roster when you walk on to the Drum. With regard to things like the Captain going a shore and a few others, I ll see if we can get actual sources on those items.
All of that was taken from actual logs and historical documents and is verifiable. We are also producing a documentary with never before seen interviews from a number of Vets from the USS Drum Wanted to find a way to plant my nephew at the kybd with unlimited torpedo reloads as he s a tad young to get the entire game.
Maybe in a full harbor, heh. Dunno how to script or mod myself sorry to say. Unlimited torpedoes and instant reloading. Then spray torpedoes everywhere in the general direction of a huge jap task force.
Didn t get the answer i was looking for at the other forum so i tried here. I knew no matter how careful i was i d get some flak but this country is big on free speech and so am i JL. I don t think that it can be done, but I m hoping someone will come along and prove me wrong.
People have made the reloads go faster, but I don t recall seeing unlimited reloads. As you say, it would be nice for learning and for kids. Ok cool, thanks for the mine info. Yeah I can t even imagine how rancid the smell got below decks having not bathed for 2 months.
Never seeing the sky probably did a number to a man s mental stability too. You know just on a side note, I just hit my personal best the other day in the east china sea playing with RFB 2. I did a ton of plotting, observing, and double checking.
I m never using those stupid dials to guesstimate speed ever again. Convert Coreldraw X3 Activation Code trail version to full software. Explore design, layout, photo-editing and web design tools. The official website for Corel Software.
Then create serial number and input it into. Elliott Smith, born August 6, in Omaha NB, Horoscope, astrological portrait, dominant planets, birth data, heights, and interactive chart. Convert Horoscope Explorer 3.
Horoscope Explorer Pro 3. Convert Horoscope Explorer Pro 3. WOW Horoscope Interpreter 3. Serial horoscope explorer Pro. Found results for Horoscope Explorer 3. We have the largest serial numbers data base.
Found results for Horoscope Explorer crack, Your search for Horoscope Explorer may return better results if you avoid searching for words such as:. Did you lose the driver disc that came with your Brother HL hardware. Published January Electrical Contractor 3 Bethesda Metro Center, Suite, Bethesda, Find essential electrical hand tools from Grainger to help simplify professional electrical jobs.
Uninstall the driver then reinstall aagain and see if the same problem exists. A stunning MMS featuring an alleged Ganga TV serial actress mouthing vulgar dialogues in a mock product advertisement.
This website contains sexually explicit adult content, including still and moving images of nude adults, adults engaged in sexual acts, and other sexual material. Entering this website is prohibited if you are not at least 18 years old 21 in some areas or if you are visiting this website from the jurisdiction of any municipality, city, state, country, or other governmental entity where viewing adult content is prohibited by law.
You are under an affirmative legal obligation to leave this site NOW if you are under 18 21 in some areas, if visiting this adult website is prohibited by law, or if you will be offended by adult content.
Enter this website only if you accept each and every provision of the following agreement:. By accepting this Agreement and thereby entering this adult website, I hereby swear and affirm under oath, represent and warrant that the following statements are true:.
I am not visiting this website from the jurisdiction of any municipality, city, state, country, or other governmental entity where viewing adult content is prohibited by law. I understand the standards and laws of the community from whence I am visiting this adult website, and I have made every reasonable effort to determine whether viewing adult content is legal - I have determined that it is not illegal for me to visit this adult website.
I will not allow any person under 18 21 in some areas years old to view any adult content from this website. I will not allow any person who is under the jurisdiction of any municipality, city, state, country, or other governmental entity where viewing adult content is prohibited by law, view any adult content on or from this website.
I am entering this website because it has adult content. I do not find adult content offensive or objectionable. I believe that as an adult I have the right to choose what I see and read, and I am choosing to enter this adult website to view adult content.
By entering this website, I agree to release, discharge, and hold harmless the providers, owners and creators of this website from any and all liability which might arise from viewing or reading the adult content on this website.
I will not copy, upload, transmit, transfer, distribute, publish, modify or use for any commercial or other purpose any of the material on this website, including the underlying HTML source code, without permission in writing and signed by the owner of the material.
Bookmarking or directly accessing any other page on this website and bypassing this Agreement shall constitute an implicit acceptance of this Agreement. If I use these services in violation of this Agreement, I understand I may be in violation of local, state, federal, international or other laws.
Tamil tv serial actress ammu hot tv serial actress bhavana hot tv serial actress bikini tv serial actress bhavana telugu tv serial actress bhavana hot telugu tv. The first section presented analysis tools whereby the acceptability of manual handling MH requirements can be calculated.
When physical demands associated with a MH task are determined to be unacceptable, the use of a mechanical assist can be evaluated. In this section, over seventy MH product types, including manipulators, lift tables, drum handling equipment, etc.
Matrices for lift tables and manipulators are presented on the following pages. Following the matrices, a table is presented describing ergonomic design guidelines associated with fork trucks. Advance Lifts manufactures powered lift tables and dock lifts.
The lift tables range in height from 6. Portable as well as fixed location units are available. Air Technical Industries manufactures a wide variety of material handling equipment. The X-Light Duty scissor lift carts have capacities ranging from lb, lowered heights of 10, and raised heights ranging from 24 to 44 depending on model.
These lifts have hydraulic lifting action, either manually, electric, or battery activated. Roller decks are optional. Lift-Smart is a device for lifting, lowering, moving, positioning, and holding loads. Low positions range from floor level to 9 and a travel distance of 38 is standard.
Capacities range from lb. American Manufacturing Company, Inc. The collapsed heights of the tables range from 5 to 12 and the vertical travel distances range between 25 and 72, depending upon the model. Optional equipment such as turntable decks, roller decks, safety skirts, and horizontal travel are available.
Bishamon Industries Corporation manufactures scissor lifts, adjustable height carts, turntables, and upenders. The hydraulic adjustable height carts range in capacity from to lb and range in vertical height from 8. C H Distributors, Inc.
Adjustable height carts, stackers, and portable scissor lift tables are available from manufacturers such as Presto, Southworth, Wesco, Bishamon, Genie, Eurokraft, and Lift-Rite. Carico Systems manufactures carts and containers.
Wire mesh carts offer visual inventory, are completely collapsible, and have optional shelves and front drop gates. Containers with optional casters are available which have spring-loaded bottoms. The base floats up and down so that top level of products are level with the gate opening as products are placed into or removed from the container to minimize bending.
Castle Industrial Ergonomics, Inc. They distribute adj-ht carts from Lee Engineering. Cherokee Products Corporation is a distributor of material handling equipment, tool balancers, and anti-fatigue mats. The Southworth Dandy Lift transports and lifts weights up to lb to maximum heights of Ergo Source distributes a variety of ergonomic products ranging from office equipment to mechanical assists and hand tools.
An adjustable-height push cart is available with a lb capacity and an adjustment range of A foot-operated hydraulic jack is used to make height adjustments 24 strokes required across adjustment range. Global Equipment Company is a distributor of industrial seating and workstation equipment as well as material handling equipment A wide range of carts are available, including service, stock, utility, and instrument carts, carts with sliding shelves, wire shelf trucks, and a 24 adjustable height cart.
Grainger is a distributor of industrial and commercial equipment and supplies. The Zero-Creep lift system provides indefinite load holding capabilities. The collapsed heights of the lifts range between 6 and Vertical travel distances of 32, 50, or 60 and capacities ranging between and 12, lb are available.
Accessories and options include turntable, conveyor, and tilting tops as well as rollers. Cranes, drum handlers, hand trucks, lift tables, work positioners, vacu-lifts, robotics, tilt tables and many other material handling equipment are available.
Lee Engineering Company manufactures lift and turntables, adjustable height carts, and pallet trucks. Mechanical, electro-mechanical, and hydraulic scissor lift tables are available, ranging in capacity from lb.
Eight more commercial antivirus utilities proved effective enough to earn an excellent four-star rating, and another eight earned 3. Almost all of these products are traditional, full-scale, antivirus tools, with the ability to scan files for malware on access, on demand, or on schedule.
A couple are outliers, tools meant to enhance the protection of traditional antivirus. As for just relying on the antivirus built into Windows 8. In the past, Windows Defender has performed poorly both in our tests and independent lab tests, though it did score a win in September and again last month.
Maybe Microsoft s slump is ending. I take the results reported by independent antivirus testing labs very seriously. The simple fact that a particular vendor s product shows up in the results is a vote of confidence, of sorts.
It means the lab considered the product significant, and the vendor felt the cost of testing was worthwhile. Of course, getting good scores in the tests is also important. I follow six labs that regularly release detailed reports: Tests by the first three are based on simple threat-recognition, while the last three attempt to simulate real-world malware-attack scenarios.
I ve devised a system for aggregating results from the labs to yield a rating from 0 to 5. I also subject every product to my own hands-on test of malware blocking, in part to get a feeling for how the product works.
Depending on how thoroughly the product prevents malware installation, it can earn up to 10 points for malware blocking. My malware-blocking test necessarily uses the same set of samples for months. To check a product s handling of brand-new malware, I test each product using extremely new malware-hosting URLs supplied by MRG-Effitas, noting what percentage of them it blocked.
Products get equal credit for preventing all access to the malicious URL and for wiping out the malware during download. Some products earn absolutely stellar ratings from the independent labs, yet don t fare as well in my hands-on tests.
In such cases, I defer to the labs, as they bring significantly greater resources to their testing. Antivirus products distinguish themselves by going beyond the basics of on-demand scanning and real-time protection.
Some rate URLs that you visit or that show up in search results, using a red-yellow-green color coding system. Some actively block processes on your system from connecting with known malware-hosting URLs or with fraudulent phishing pages.
Software has flaws, and sometimes those flaws affect your security. Prudent users keep Windows and all programs patched, fixing those flaws as soon as possible. The vulnerability scan offered by some antivirus products can verify that all necessary patches are present, and even apply any that are missing.
You expect an antivirus to identify and eliminate bad programs, and to leave good programs alone. What about unknowns, programs it can t identify as good or bad. Behavior-based detection can, in theory, protect you against malware that s so new researchers have never encountered it.
However, this isn t always an unmixed blessing. It s not uncommon for behavioral detection systems to flag many innocuous behaviors performed by legitimate programs. Whitelisting is another approach to the problem of unknown programs.
A whitelist-based security system only allows known good programs to run. This mode doesn t suit all situations, but it can be useful. Sandboxing lets unknown programs run, but it isolates them from full access to your system, so they can t do permanent harm.
These various added layers serve to enhance your protection against malware. Firewall protection and spam filtering aren t common antivirus features, but some of our top products include them as bonus features.
In fact, some of these antivirus products are more feature-packed than certain products sold as security suites. Among the other bonus features you ll find are secure browsers for financial transactions, secure deletion of sensitive files, wiping traces of computer and browsing history, credit monitoring, virtual keyboard to foil keyloggers, cross-platform protection, and more.
And of course I ve already mentioned sandboxing, vulnerability scanning, and application whitelisting. Which antivirus should you choose. You have a wealth of options. Kaspersky Anti-Virus and Bitdefender Antivirus Plus invariably rate at the top in independent lab tests.
And its unusual behavior-based detection technology means Webroot SecureAnywhere Antivirus is the tiniest antivirus around. We ve named these four Editors Choice for commercial antivirus, but they re not the only products worth consideration.
Read the reviews of our top-rated products, and then make your own decision. Unknown programs in folders commonly used by malware just can t launch, and programs that do run can t make changes to sensitive system areas.
It definitely works, but you ll have to do some finagling to install or update valid programs. Read the full review. It can definitely prevent installation of new malware, as long as you don t erroneously override its block.
However, the average user may find managing its protection to be a chore. Its biggest competitor may be the company s own cross-platform multi-device suite, which secures an unlimited number of Windows, Mac OS, and Android devices.
Download the best antivirus for Windows from Bitdefender and get protection against viruses anti spyware without slowing down your PC. This article really needs no introduction. There are many free anti-virus programs on the market, and you want to sort the wheat from the chaff.
Looking for free Open Source Antivirus for Windows. Download ClamWin Free Antivirus and get free virus scanning and free virus definition updates. Top 10 Paid Antivirus Programs for The battle for antivirus software supremacy is a close one.
Ultimately, Norton Antivirus ekes out a narrow. Avast Free Antivirus is an antivirus that needs no introduction. Praised by many users for its PC protection, Avast no longer avast. Found results for Profili 2 crack, serial keygen.
Our results are updated in real-time and rated by our users. No registration is needed. Just download and enjoy. The new Profili 2 Pro Keygen is. Profili 2 serial numbers, cracks and keygens are presented here. The download is free, enjoy.
If you search for Profili 2 Crack, you will often see the word crack amongst the results which means it is the full version of the product. What is a Serial. Advanced search by filtering based on library, name, thickness, camber and other geometrical parameters.
Mix of two airfoils. This lets you to create a new airfoil by mixing two selected from the database. You can also define the mixing percentage. With this function you can generate the intermediate airfoils in a wing with different ones at root and tips.
So you can then generate the polars and check the aerodynamic of your new wing. Modification of airfoil external shape and camber line coordinates with the mouse, with CAD-like interface. Pre-processed polars by XFoil for all the airfoils of the database at 20 predefined Reynolds numbers from 30, to, More then 40, polars in the database, ready to use.
Add rectangular spars according to different positioning way delta-box optimized, on the upper-lower point, on a defined point of the chord. Now you can also generate all the ribs not only for a trapezoidal wing, but also for an elliptical one.
Profili 2 - cracked versions I received several e-mails informing me about a few web sites including a link to cracked versions of Profili, Profili Pro or serial. I received several e-mails informing me about a few web sites including a link to cracked versions of Profili, Profili Pro or serial generators, but these include viruses inside.
Other viruses start to work some time later, destroying your data or part of them, slowing down the computer, installing malware and so on. Often these web sites require a registration. In this way they ask for your data or email.
Then they will sell them for commercial use or worst. Very often they offer then a fake download. Sign in to add this video to a playlist. What is an Activation Key. An activation key is a unique key that recognizes you as a valid user.
Every key is valid for one email address only. Movavi Video Suite is all you need for you video processing and multimedia needs. The software comes with built in powerful tools that allows you to convert. If after renewing your license you receive a new License Key, but require a Username and Password for use with older ESET products, it is possible to convert the License Key for usage with these older products.
After you receive your License Key, it can be used for all version 6 and later products purchased under the corresponding license. These credentials were sent to you in an email when you originally purchased your ESET product s.
To have your Username and Password resent, select the check box next to Resend license email. If you receive the notification You have entered invalid license credentials, we recommend that you recover your license information and verify that you are entering it correctly.
Your new License Key will be provided in the following window. We cannot respond to feedback from this form. Requests for assistance should be submitted through your normal support channel.
Homeland Security virus can also be called as U. Department of Homeland Security virus is dangerous ransomware, which belongs to cyber criminals. Reveton Trojan you can also find it named as Trojan: A is a harmful program, ransomware, that presents about itself for its victim.
Download 10 Antivirus terbaik dan gratis untuk HP Android, antivirus untuk ponsel Android ini ada yang versi gratis dan juga versi premium. Komputer dengan sistem operasi Windows tidak akan dapat dipisahkan dari produk antivirus.
Umumnya sistem operasi windows hanya memerlukan satu produk antivirus untuk menjaganya dari serangan virus yang tidak diinginkan. Sekilas pandang, hal ini terlihat sangat meyakinkan, karena ada dua atau lebih antivirus yang akan melindungi komputer dari serangan virus.
Jika dilihat lebih jauh, menggunakan dua atau lebih produk antivirus akan membuat performa komputer menurun secara drastis. Proses kerja komputer akan melamban dan mungkin dapat mengakibatkan kesalahan pengidentifikasian virus.
Lebih buruk lagi dapat menyebabkan computer crash ataupun bluescreen. Apabila hal ini telah terjadi, satu-satunya jalan adalah menghapus salah satu produk antivirus. Umumnya menghapus atau menguninstall program dapat dilakukan di control panel windows.
Ketika hal ini terjadi, kita dapat menggunakan antivirus removal tool untuk menghapus paksa antivirus yang terpasang. Berikut adalah removal tools untuk beberapa produk antivirus luar. Selain memang meminimalisir masuknya virus, antivirus juga dapat mengeliminasi ketakutan beberapa orang secara psikologis.
Tak jarang bahkan beberapa orang. It appears that Symantec has decided to drop t. Supports the following versions of Symantec antivirus software: Symantec AntiVirus Corporate Edition provides scalable, cross-platform virus protection for workstations and network servers throughout the enterprise.
The Symantec Antivirus Corporate Edition All you need is a TV. Download VLC media player now from Softonic: More than downloads this month. Download VLC media player 2. Below are our top streaming-media device picks.
We ve limited the list to standalone streaming boxes and sticks, but be aware that lots of other home theater products are competent streamers these days, from Blu-ray players to game consoles to TVs themselves.
Jul 30, License: No special requirements Publisher: After our trial and test, the software is proved to be official, secure and free. Main feature of this tool is that it works in hidden mode just by using the setting button.
Tool easily lock and unlock your personal files and documents. It allows you to lock the folder by providing password. If anybody wants to access that folder then it prompts for entering the password. Thus this password protected utility keeps your data files safe from others.
To lock any folder, you don t need to cut and paste that files or folder in any separate special folder. You only need to right click on the folder, and click on the V2SL Folder Lock, a window will appear to Ask you to enter the password.
After entering the password you can lock or unlock that folder. You can set your desired password for folder you want to protect. Utility provide security by encrypting the folder data. Folder Security lock software can work in hidden mode by using setting button.
In hidden mode you can use Start -- Run -- Now type Flock to lock or unlock. Software can be launched by right clicking on any folder. Please be aware that Brothersoft do not supply any crack, patches, serial numbers or keygen for V2 Softlogic Folder Security Lock, and please consult directly with program authors for any problem with V2 Softlogic Folder Security Lock.
V2 Softlogic Folder Security Lock 1. Jul 30, - Please be aware that Brothersoft do not supply any crack, patches, serial numbers or keygen for V2 Softlogic Folder Security Lock, and please. We manufacture Fishing Rod Holders and Trolling Systems to accommodate any kind of boat and any kind of fishing.
V2Softlogic Folder Security lock can work in hidde. Posted on 28 September by Michael. Portable recover excel password - Excel Password Unlocker 4. Excel Password Unlocker is a Portable and High-eff. Pixillion Image Converter Software Free 2.
Posted on 18 February by James Park. Learn how to register Driver Detective including important screenshots, which will help you understand the registration process even better. Driver Support can assist your search for drivers at the respective manufacturers website for free.
Driver Support s full driver installation functionality. It looks like you have Javascript disabled or NoScript plugin. In order to keep the content of this website free we must display advertisements on it that require Javascript.
If you want to view the content of this website the author wishes that you to turn Javascript back on or turn off NoScript. This message will go away once Javascript is enabled and you press the Back button. One of the easiest and safest ways to register Driver Detective is through SafeCart, a reliable and trusted payment processing system.
After a simple registration and payment process, you will be able to obtain a license key for Driver Detective software and enjoy its full benefits. If you would like to learn more about the Driver Detective registration process, the information and screenshots below are very helpful.
Once you follow the link, you will reach the first step of the registration process. Some may wonder Why do I need to provide my email address. The email is required so that you can receive your registration key and receipt.
Also, in the email, you will be provided with the username and password to access your online account, including online backup of your hardware drivers. Every SafeCart order is backed by day money-back guarantee.
If you are not happy with your purchase, you will receive a full refund within 60 days. A one-year license is By checking the small box, you can upgrade this to two years for only an extra 9. It s worth mentioning that this license allows you to install Driver Detective to up to 10 computers.
Considering the benefits and time and energy you will be saving, the license is worth every penny paid for it. Pay with Credit Card or PayPal: For your convenience, you have the option to pay with your credit card or via your PayPal account if you have one.
The next screenshot shows what you will be seeing if you click on the Credit Card button and select the two-year option. It s worth mentioning that SafeCart will not store your credit card number, so you can feel absolutely confident that your order will be secure.
After you fill out the credit card information and click the Process Order NOW button, and if the process is successfull, you will receive two emails:. Driver Detective Purchase Acknowledgment: Providing you with your license key, final registration steps, and your username and password to access your online Driver Detective backup and support account.
Providing you with your payment s receipt, including your receipt ID, which you will need in case you want to refund your purchase. As mentioned already, you will receive final registration steps in your email, but we will also summarize them here:.
If you haven t done so already, Open Driver Detective. Click Start, click Programs, and then click Driver Detective. Click on the Activate button. At that point, Driver Detective will be registered and you will be ready to enjoy its full benefits.
How to Uninstall Driver Detective. Driver Detective promises a free scan that will fix all your problems. As with so many other online offers, it turns out that all. Driver detective registration key, driver detective activation key free, activation key software, driver detective activation key crack, Driver detective 9 keygen.
World s most popular driver. USB devices are known as Plug and Play, which means Windows usually detects devices when they are plugged in and, if necessary, automatically installs drivers. All drivers available for download have been scanned by antivirus program.
Please choose the relevant version according to your computer s operating system and click the download button. The device can work with any. During this process, the Download. Norton Ghost 15 Keygen keygen Tags: Windows 7 compatible Norton Ghost 15 now offers 25G.
This version also introduces a new cold imaging feature that images computers without. Norton Ghost 15 is a robust and professional-grade backup solution for both home users and small businesses. Ghost, lost or damaged files can be recovered and restored in the event of a system failure, even if the computer s.
It also allows backup of an entire system or specific files and folders while saving. Norton Ghost is also flexible, allowing users to decide when to back up. Norton Ghost has been the essential imaging and recovery product since, said Dave Cole, senior director of consumer.
Consumers PCs have never been more central to people s lives, or more at risk due to cybercrime and. Ghost 15 not only is a powerful disaster recovery tool, but also it adds important features such as.
Windows 7 compatibility and Blu-ray Disc support to keep current with the way people are using their computers today. World s most popular driver download site. Law Firm Runs on Dictations: Law firm in Limburg successfully switches over to digital dictation.
Lijnrecht, a law firm in Tongeren, has. The Microsoft Bluetooth Notebook Mouse can operate While Microsoft wants you to install its custom driver software, the mouse. The scroll wheel does not work in Windows.
With ThinkOutside s Stowaway Travel Mouse you can easily navigate your The Stowaway travel mouse includes cutting edge software drivers that support. These scripts now depend on freemangordon s mouse driver and keyboard layouts.
BT Mouse think outside stowaway travel mouse and my BT. Think Outside Stowaway Travel Mouse. Bluetooth Notebook Mouse Limited Warranty pdf Download. Limited Warranty xps Download. Product Guide pdf Download.
You can also use the mouse. Find great deals on eBay for Stowaway Bluetooth Keyboard sony vaio ux. Skip to main content. Think Outside Bluetooth Travel Mouse. What operating system are you using. Mouse and Keyboard Center 2.
Stowaway Bluetooth Travel Mouse. Download Now Secure Download. Stowaway is a trademark of Think Outside. Mice and Pointing Devices. Find great deals on eBay for stowaway keyboard igo keyboard. Enter your search keyword. Unfortunately, there doesn t seem to be a Windows 7 update for Stowaway Mouse driver.
Not sure why the Bluetooth discovery process would be different. Software, drivers, manuals, and more for your Microsoft device. The Comfort Curve Keyboard, from Microsoft, is ergonomist approved and helps provide a more natural wrist position.
If this is your first visit, be sure to check out the FAQ by clicking the link above. You may have to register before you can post: The term M1A is a proprietary title. I was perusing a website and noted that some FN s from Belgium had been imported into the U.
A listing of their serial numbers was. All mauser serial numbers are four digit. When they reach, they bump up the letter one step, and start over again. This makes it very difficult to figure out.
Below you will find a list of discussions in the Reference forums at the M14 Forum. The Reference forum is for discussion of: M14 M1A Reference Guides. It is the big rig that you are going to drive here in this particular online game.
Drive to go around delivering goods but you have to be careful least you damage. Driving skills and balancing skills come under the test while playing these games. Driver 3 for PlayStation 2 Cheats - IGN has all the codes, cheat codes, unlockables, easter eggs, achievements, hints, tips and secrets.
Driving them at high speed probably. Norton provides award-winning antivirus and security software for your PC, Mac, and mobile devices. Get Norton software and enjoy a peace of mind when you surf. Norton Antivirus stops viruses, worms, spyware, bots, and more - Keeps your system protected against all types of malicious threats.
Download Norton instantly. If you re looking for FREE antivirus and doesn t mind the 90 days trial period, Norton has some really good collection of 90 days trial antivirus. Norton AntiVirus, developed and distributed by Symantec Corporation, was providing malware prevention and removal during a subscription period.
See the latest information on computer virus attacks and their removal. McAfee is the leader in internet security and virus detection. Keep up to date on the most. Learn what steps to take for network incident response following the download of bad antivirus update, or DAT, files, including creating a network outage reporting.
McAfee LiveSafe service provides trusted protection so you can shop, surf and keep all your devices secure online with the convenience of a single subscription. October 11, Updated: The below detailed steps will guide you through the express uninstallation of McAfee Antivirus.
McAfee is the world s largest dedicated security technology company. Delivering proactive and proven solutions and services that help secure systems and networks around the world, McAfee protects consumers and businesses of all sizes from the latest malware and emerging online threats.
Our solutions are designed to work together, integrating anti-malware, anti-spyware, and virus protection with security management features that deliver unsurpassed real-time visibility and analytics, reduce risk, ensure compliance, and help businesses achieve operational efficiencies.
Backed by an award-winning research team, McAfee security technologies use a unique, predictive capability that is powered by McAfee Global Threat Intelligence enabling home users and businesses to stay one step ahead of online threats.
McAfee enables users to safely connect to the Internet, and securely surf and shop the web. Additionally, McAfee s virus removal service helps consumers easily clean viruses and spyware from PCs all from the comfort of their homes.
McAfee solutions deliver the highest levels of threat visibility and anti-malware protection, including a comprehensive defense for systems, networks, data, and endpoints. McAfee s complete security solutions extend beyond virus software.
Backed by McAfee Global Threat Intelligence, our solutions help companies enhance visibility into their security postures, allowing business to embrace Web 2. A single, integrated solution, complete with a built-in desktop firewall, which secures systems and data against sophisticated malware, zero-day attacks, noncompliant systems, and unauthorized devices.
McAfee Network Security Platform: Our best-in-class intrusion prevention system that delivers real-time defenses against known, zero-day, denial-of-service DoS, distributed denial-of-service DDoS, SYN flood, and encrypted attacks.
McAfee Enterprise Mobility Management: A revolutionary security solution that helps businesses offer employees mobile device choice including iPhones, iPads, and Android devices while providing secure and easy access to corporate mobile applications.
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. This is a general instruction for updating your TT.
It is dedicated to users who are inexperienced in updating their TT, but are computer literate. After losing all my data post using TomTom Home and like a fool not having done a seperate backup I have had to re format my SD card and start a new install.
The title branding programs typically have two objectives: A deterrent to auto theft If a vehicle is a complete loss due to an accident, its serial number. How to Look up Vehicle Vin Numbers.
The vehicle identification number, more commonly referred to as the VIN, can tell you everything about a vehicle, from the. What secrets do those What is a VIN. VIN Vehicle Identification Number is a unique universal serial number issued to every vehicle by the manufacturer.
Within the digit number are. Missouri law requires all motorized vessels, sailboats over 12 feet long, and gasoline powered outboard motors to be titled within 60 days of. Finally, I found a solution the solution on Windows 8. Future OS are supported via the online.
All our software are virus-free and trojan-free, all download links are from reliable sources as claimed. Monkey3 are a psychedelic rock band from Lausanne. Editing file tags in Windows Media Player is an easy way to reorganize you music, or modify the way tracks display on your MP3 player.
Follow the simple steps below. Start up Windows Media Player and open the Library. Right-click on a song in your library and select Edit. Choose what field you want to edit, make your edit and.
These tags can help programs like iTunes and Windows Media Player organize and store the music on your hard drive. If the songs whose tags you want to edit. Windows Media Player is Microsoft s media library software that allows users to play audio and view video and images on their.
Editing video is typically done by using video editing software, such as Windows Movie Maker that is available with the Vista and. A video file s metadata is a collection of data that describes the specifics of the video.
Learn how to get song. Windows Media Player, or. Get the latest weird news stories from all over the world. Find bizarre and offbeat news about people, nature and unexplained mysteries at ABC News. Rediscover Your Childhood Here are some newly updated pages.
It is based on various conflicts between four kinds of plastic army men. On his debut Automaton, the artist born Evan Reiner used recordings from Tokyo to Pasadena to create a lush electronic production.
Chris Davids and Liam Ivory the pair behind Maribou State get synthy and organic on their debut album. It may have taken seven years for the Icelandic band to release their new album, but it s well worth the wait.
The first rule of the Fight Club rock opera is you do not talk about the Fight Club rock opera. George FitzGerald and Verboten rented a cruise ship and threw a dance party on a boat this weekend.
On their most recent release, Broken Into Better Shape, the band come to terms with becoming a duo. The singer discusses the personal matters that make up Pull the Thorns from Your Heart between bites of brown rice and veggies.
Genre-bending artist who writes, sings, raps and choreographs his own songs is bound to be Flint, Michigan s most popular resident. There s no one like Amy, but these artists have similar jazz influences that make them just as unique.
I mean, I don t really care much. I ve been writing music for so long. I m just gonna keep doing what I do. Top News brought to you by EarthLink. Stay on-top of current events with the EarthLink News Channel.
Automatically download and update your HP laptop drivers. HP Driver Updates Scanner can help relieve you of worries about installing an incorrect or out-of-date. In fact, only a meager 25 percent did. In other words, the difference could easily be due to what statisticians call sampling error.
Solving this problem requires people to literally think outside the box. That is, direct and explicit instructions to think outside the box did not help. That this advice is useless when actually trying to solve a problem involving a real box should effectively have killed off the much widely disseminated—and therefore, much more dangerous—metaphor that out-of-the-box thinking spurs creativity.
After all, with one simple yet brilliant experiment, researchers had proven that the conceptual link between thinking outside the box and creativity was a myth. But you will find numerous situations where a creative breakthrough is staring you in the face.
They are much more common than you probably think. There are many theories of creativity. What the latest experiment proves is not that creativity lacks any association to thinking outside-the-box, but that such is not conditioned by acquired knowledge, i.
For example, there have been some theories such as those of Schopenhauer see his remarks about Genius and Freud see his remarks about Sublimation that propose creativity is something more like a capacity provided by nature rather than one acquired or learned from the environment.
Rather than disproving the myth, in other words, the experiment might instead offer evidence that creativity is an ability that one is born with, or born lacking, hence why information from the environment didn't impact the results at all.
It's an interesting experiment, but the author's conclusion cannot possibly follow from the results of it. In the past several decades there has been a revolution in computing and communications, and all indications are that technological development and use of information and facts technology will carry on at a speedy rate.
Accompanying and supporting the dramatic improves in the energy and use of new information and facts technologies has been the declining charge of communications as a consequence of the two technological advancements and enhanced opposition.
In accordance to Moore's regulation the processing ability of microchips is doubling just about every eighteen months. These improvements current lots of substantial options but also pose main troubles.
These days, improvements in info technological innovation are owning broad-ranging consequences across quite a few domains of culture, and coverage makers are performing on problems involving financial efficiency, intellectual property legal rights, privateness defense, and affordability of and entry to facts.
Alternatives created now will have long long lasting implications, and interest need to be paid out to their social and financial impacts. A person of the most considerable outcomes of the progress of info technologies is most likely electronic commerce above the Internet, a new way of conducting organization.
While only a couple many years old, it could radically change financial things to do and the social surroundings. Now, it affects this kind of large sectors as communications, finance and retail trade and may possibly develop to regions these types of as schooling and overall health companies.
It indicates the seamless application of data and conversation technology along the entire benefit chain of a company that is done electronically. The impacts of facts technological know-how and electronic commerce on company models, commerce, current market structure, workplace, labour industry, training, personal daily life and society as a entire.
A single essential way in which data technology is impacting work is by lowering the worth of length. In numerous industries, the geographic distribution of work is transforming substantially. For instance, some program companies have uncovered that they can conquer the tight local market place for application engineers by sending tasks to India or other nations where the wages are a great deal lower.
Furthermore, these kinds of preparations can acquire benefit of the time discrepancies so that vital projects can be labored on almost all around the clock. Thus the technologies can allow a finer division of labour between nations, which in flip has an effect on the relative need for different skills in just about every country.
The technologies permits different sorts of work and employment to be decoupled from one another. Corporations have bigger independence to locate their financial things to do, creating greater levels of competition among regions in infrastructure, labour, money, and other resource marketplaces.
It also opens the door for regulatory arbitrage: Desktops and interaction systems also promote additional current market-like kinds of generation and distribution. An infrastructure of computing and interaction technologies, furnishing hour obtain at reduced price to nearly any sort of rate and product info desired by prospective buyers, will lessen the informational boundaries to economical sector operation.
This infrastructure could possibly also supply the suggests for effecting actual-time transactions and make intermediaries these kinds of as profits clerks, stock brokers and journey brokers, whose functionality is to deliver an crucial facts backlink amongst purchasers and sellers, redundant.
Removing of intermediaries would minimize the charges in the production and distribution worth chain. The information and facts systems have facilitated the evolution of increased mail order retailing, in which items can be ordered quickly by using telephones or computer system networks and then dispatched by suppliers by built-in transportation corporations that rely thoroughly on computer systems and interaction systems to handle their functions.
Nonphysical merchandise, this sort of as computer software, can be delivered electronically, doing away with the whole transportation channel. Payments can be performed in new ways. The result is disintermediation all over the distribution channel, with expense reduction, decreased conclude-client charges, and higher gain margins.
I conduct soft skills training and outbound training for Corporates and individuals. To enhance creativity we motivate the participants to approach the problems from variety of vantage points. Even repeatedly checking the boundary conditions we are able to come up with variety of ways of solving the problem.
This is akin to checking the walls of the box. Looking inside the box for additional information, additional resources also helps. Looking at the box from bird's eye view triggers some different creative solutions.
Let us not get tied down to the mechanics but free ourselves to find the solution.
Windows download ccleaner full 7 round mock steph curry
Should you choose not to save the application, you may simply initiate the free scan by clicking the Run button on the File Download Window. I play chess with my pc, an beat it all the time, and the reasoning is I do not think logically, like the pc does. The purpose of a provisional driving permit is to allow teen drivers to practice behind the wheel under close supervision. Kapil, a prison doctor who regularly pronounces inmates dead, said he was taking a vacation day. These are earned by.
Coments:
03.04.2018 Duran:
Sulky Velky only $ w/ FREE Shipping! BRAND NEW Mower sulky / velky for Toro commercial mowers. Buy now and take advantage of our summer savings specials! Download the free trial version below to get started. Double-click the downloaded file to install the software.
14.02.2018 Tele:
Motorola driver. Motorola Modem Drivers. This site maintains listings of modem drivers available on the web, organized by company. Includes links to useful modem. Statistical Techniques | Statistical Mechanics.
08.04.2018 Kisida:
Aug 31, Want to watch this again later. Sign in to add this video to a playlist. DOWNLOAD LINK OF MS TOOLKIT OFFICE PRO. What is. With all due respect, Professor Boyd, your argument is not at all compelling. It seems that you are taking the "thinking outside the box" (TOTB) metaphor much more.
Copyright © 2017 - Download ccleaner full 7 round mock.